In our digital world, security and trust are critical. One key concept that helps ensure secure online communication and transactions is the Chain of Trust. This idea is essential for how digital certificates and Public Key Infrastructure (PKI) work, ensuring that people and devices can communicate safely. Let's explore what the chain of trust is and why it's so important.
- What is the Chain of Trust?
- Why is the Chain of Trust Important?
- How does the chain of trust work? 3 Examples
- Maintaining Trust
What is the Chain of Trust?
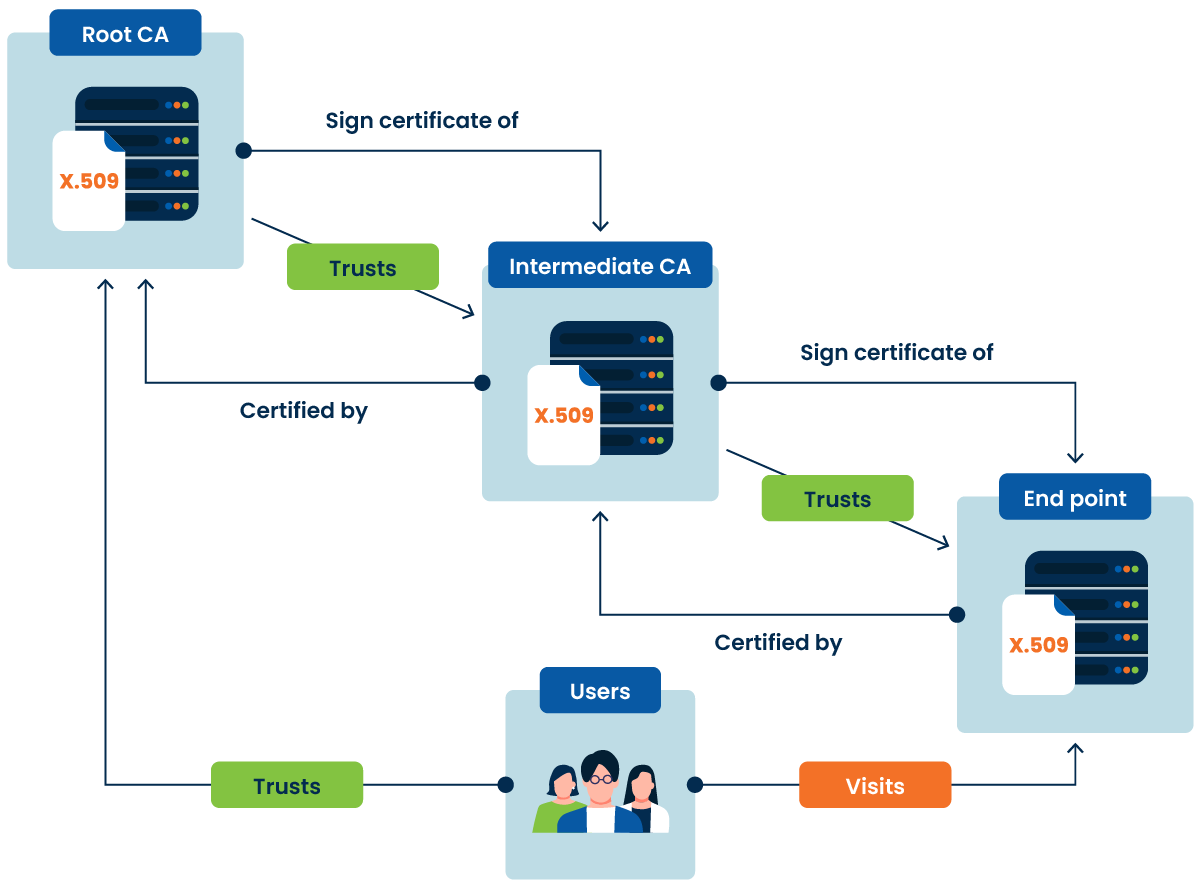
The chain of trust is essentially a trust hierarchy of certificates and certificate providers. This hierarchy is an agreement between trusted authorities in the digital landscape. As our personal and work lives, as well as our businesses assimilate further with the digital world, it is important to establish a system in order to maintain trust.
The chain of trust is a series of certificates that starts with a highly trusted root certificate, moves through intermediate certificates, and ends with the final certificate. Here’s a breakdown:
- Root Certificate Authority (CA): This is the top-level certificate. It's self-signed and trusted by browsers, operating systems, and applications
- Intermediate CA: These come after the root CA and issue certificates to the end users or further intermediate CAs. They add extra layers of security
- End-Entity Certificates: These are the certificates given to the actual users, devices, or servers that need secure communication
Why is the Chain of Trust Important?
There are three primary ways in which the chain of trust provides digital trust:
- Authenticity: It verifies that entities are who they claim to be, preventing impersonation and fraud
- Security: By creating a multi-layered trust hierarchy, it adds robustness to the security framework, making it harder for attackers to compromise any stage of the digital journey
- Confidence: Users feel more secure conducting transactions and sharing sensitive information online, knowing that a trusted system protects them
For example, when you enter your credit card information on a secured e-commerce website, the chain of trust ensures that your data is encrypted and safe from prying eyes.
How Does a Chain of Trust Work? 3 Examples
To better understand how the chain of trust works in real-world scenarios, let's look at a few specific examples where this concept is critical:
1. Software Distribution and Code Signing
Scenario:
You are downloading a new update for a popular software application.
Chain of Trust in Action:
- Root CA: A trusted root CA, such as GlobalSign, is recognized by your operating system.
- Intermediate CA: GlobalSign issues an intermediate certificate to the software company.
- End-Entity Certificate: The software company uses this intermediate certificate to sign the software update.
When you download and attempt to install the update:
- Your operating system checks the digital signature of the software.
- It verifies the signature against the chain of trust, starting from the software’s signing certificate, through the intermediate CA, to the root CA.
- If the chain is valid, your operating system allows the installation.
This process ensures that the software update is legitimate and has not been altered, protecting your system from malicious software.
2. Secure Online Shopping (SSL/TLS)
Scenario:
Imagine you’re shopping online on a website called "SecureBuy.com."
Chain of Trust in Action:
- Root CA: A trusted root certificate authority, such as GlobalSign, is pre-installed in your browser's list of trusted root certificates.
- Intermediate CA: GlobalSign issues an intermediate certificate to SecureBuy.com.
- End-Entity Certificate: SecureBuy.com uses this intermediate certificate to issue an SSL/TLS certificate for their website.
When you visit SecureBuy.com, your browser:
- Checks the SSL/TLS certificate presented by SecureBuy.com.
- Verifies the certificate against the chain of trust, tracing back from SecureBuy.com’s certificate to the intermediate CA’s certificate, and finally to the root CA.
- If the chain is valid, the browser establishes a secure connection, indicated by a padlock icon in the address bar.
This process ensures that you are indeed connected to SecureBuy.com and not an imposter site, protecting your personal and payment information.
3. Email Encryption and Signing (S/MIME)
Scenario:
You receive an email from your bank with sensitive financial information.
Chain of Trust in Action:
- Root CA: A trusted root CA, such as GlobalSign, is recognized by your email client.
- Intermediate CA: GlobalSign issues an intermediate certificate to the bank.
- End-Entity Certificate: The bank uses this intermediate certificate to issue an S/MIME certificate for its email system.
When you receive the email:
- Your email client checks the digital signature on the email.
- It verifies the signature against the chain of trust, starting from the bank’s S/MIME certificate, through the intermediate CA, to the root CA.
- If the chain is valid, your email client confirms that the email is genuinely from your bank and that it has not been tampered with.
This process ensures the integrity and authenticity of the email, allowing you to trust the information it contains.
These examples illustrate how the chain of trust is applied in various scenarios to ensure security and trustworthiness. Whether you’re shopping online, receiving secure emails, or downloading software, the chain of trust plays a crucial role in protecting your data and ensuring that the entities you interact with are legitimate. As a certificate authority, maintaining the integrity of the chain of trust is vital for fostering a secure digital environment.
Maintaining Trust
For the chain of trust to work well, certificate authorities must follow strict standards and practices. This includes:
- Thorough Validation: Ensuring entities getting certificates are thoroughly checked.
- Regular Audits: Conducting audits to maintain compliance with standards.
- Transparency: Being transparent about practices and any security incidents.
“77% of organizations say that improving their certificate and key management practices has helped them avoid compliance issues and enhance security. (Source: Ponemon Institute’s 2023 Global Encryption Trends Study.)”
The chain of trust is crucial for digital security, supporting the trustworthiness of online communications, transactions, and software. By creating a hierarchical and verifiable structure of certificates, it ensures that people and devices can interact securely. By choosing GlobalSign, you are investing in a secure future. Trust in our expertise, rigorous validation processes, and commitment to transparency. Let us help you build a strong chain of trust that protects your business and customers.
Get Started Today!
Contact us to learn more about our certificate solutions and how we can help you strengthen your digital security. Secure your trust with us and ensure your communications and transactions are protected from today's evolving cyber threats.









