Editor's Note: This article was originally published in October 2021. As of 2024, it has been reviewed and updated in accordance with the latest standards/conventions for Root Certificates.
In a perfect world, every single client that has been given a reasonable amount of warning about the impending root CA certificate expiration will never miss it and upgrade their software as necessary. But as we all know, the reality isn’t always as pleasant.
In this article, we will talk about what happens if your CA’s root certificate expires before yours do and what you can do to resolve the issues.
What is a root CA certificate and how does it work?
Certificate Authorities (CAs) are trusted entities that help secure and authenticate digital identities by issuing digital root CA certificates.
Root CA certificates obtained from CAs are used to encrypt the connections between systems, networks, and devices. When creating a website for the first time, it must have an SSL/TLS certificate. Likewise, email communications can be encrypted and digitally signed by obtaining Secure Email or S/MIME certificates.
In a certificate hierarchy, there are three branches:
- Root Certificate
- Intermediate Certificate
- End-entity Certificate
To have a better understanding of the certification path, here’s a representation of GlobalSign’s SSL/TLS Root CA Certificate Hierarchy:
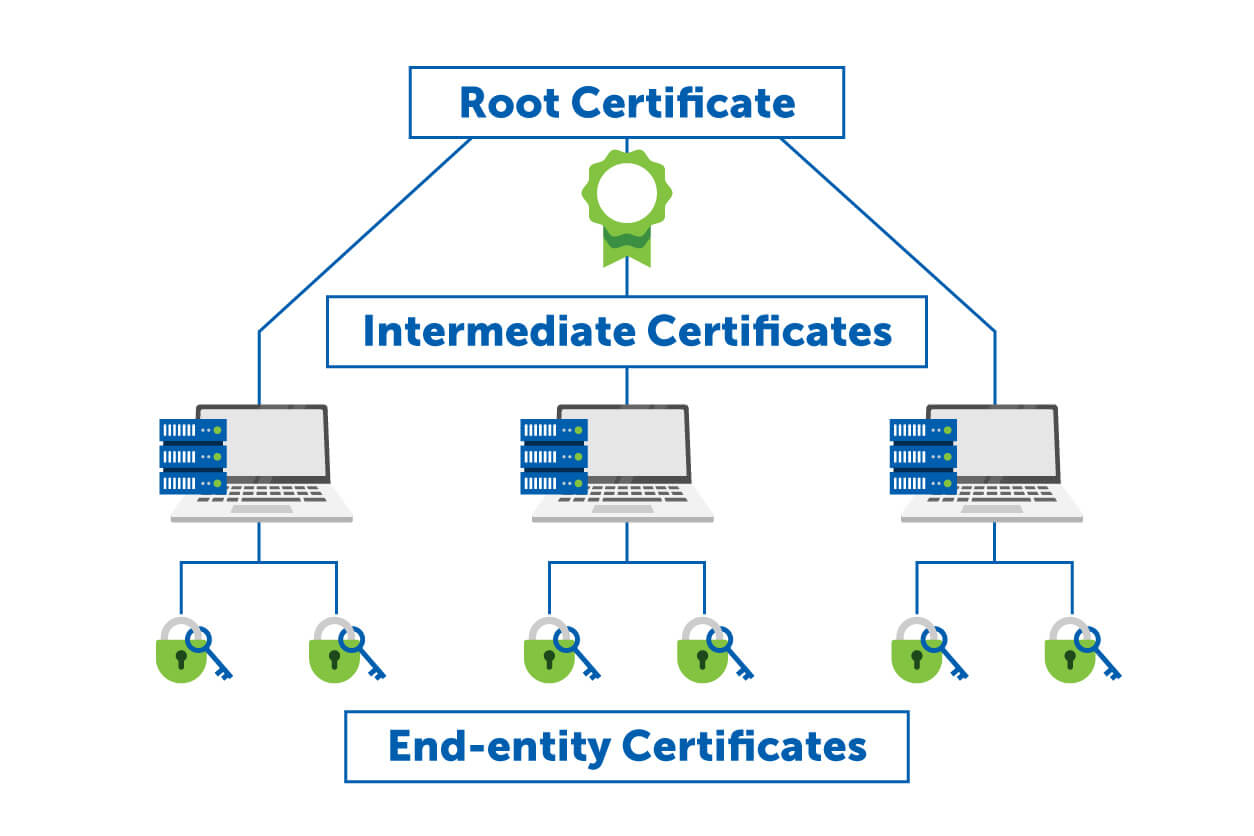
In this hierarchy, there’s an End-entity certificate on one end and the CA’s Root certificate on the other, while the Intermediate certificate is in between. When someone visits your website, the browser is going to navigate through this entire chain—from the end-entity certificate to the intermediate certificate up to the root certificates, validating each one along the way.
Understanding Root Certificates
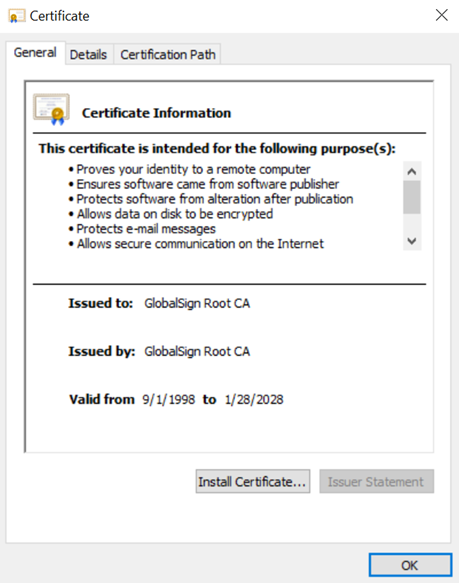
A root certificate is a public key which identifies the Certificate Authority (CA). It is self-signed and the issued “to and by” field is going to match with a longer validity period. They are kept as secure as possible as they provide the root of trust for the entire organization. If a malicious party gets their hands on the root CA certificate and private key, it is a huge breach as they can begin issuing certificates that are then implicitly trusted by the organization and users worldwide.
Root CA certificate is the trust anchor when issuing digital certificates. It is at the top of the certificate hierarchy. Computers, devices, and browsers determine which root certificates they trust in its certificate store or trust store. If your issuing CA is on the list, it is then trusted.
Pictured below is the GlobalSign Root CA certificate:
Intermediate Certificates
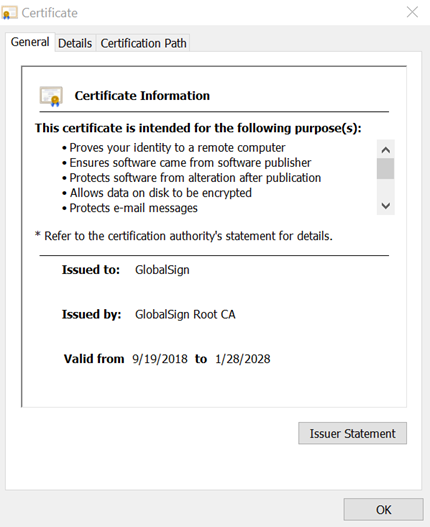
Intermediate certificates are the dividing layer between root and end-entity certificates. If root certificates are used to issue intermediate certificates, then intermediate certificates are used to issue a client’s certificate. They are also used to issue different types of certificates such as SSL/TLS certificates, document signing certificates, secure email certificates, code signing certificates, etc.
GlobalSign Intermediate Certificates
GlobalSign offers a range of intermediate certificates to suit your organization's requirements.
Our intermediate certificates are issued by our highly secure root certificate authority, ensuring the highest level of trust and reliability.
Key Benefits of GlobalSign Intermediate Certificates:
-
Enhanced Security: Benefit from the protection of our robust root certificate infrastructure.
-
Scalability: Manage your certificates efficiently, even in large organizations.
-
Customization: Create custom intermediate certificates to meet your specific needs.
-
Global Trust: Enjoy widespread recognition and trust from browsers, applications, and devices worldwide.
Here are some examples of an intermediate certificate from GlobalSign:
Learn more about GlobalSign intermediate certificates
End-entity Certificate
End-users using the certificate will be issued certificates signed by an intermediate certificate authority (CA). Computers and devices determine the trustworthiness of these certificates by verifying the issuing intermediate CA. They then verify if the root certificate of this intermediate CA is trusted and present in their certificate store.
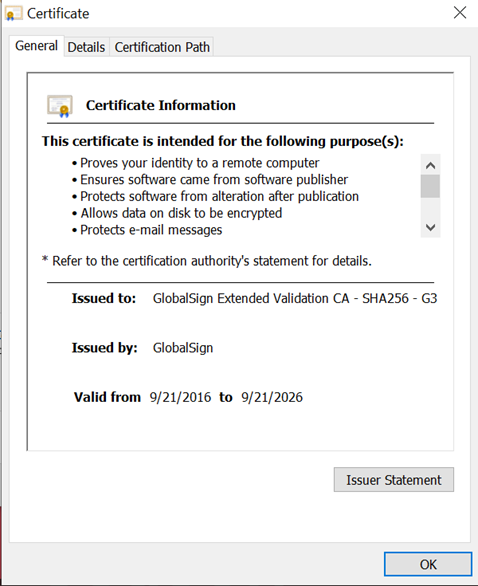
Below is an image of an SSL certificate issued to one of GlobalSign’s websites. We can see it was issued by the GlobalSign Extended Validation CA - SHA256 - G3 pictured previously.
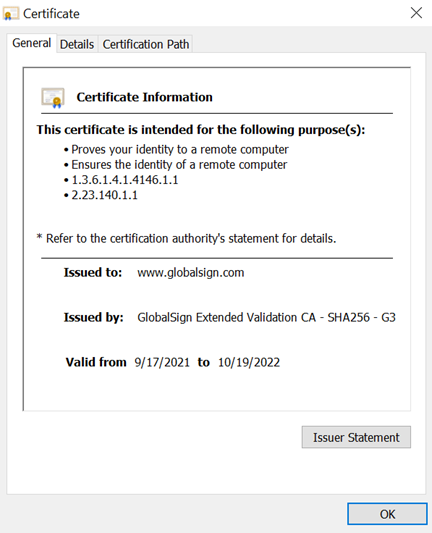
Your certificate’s certification path will often look like this:
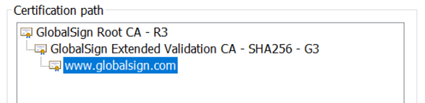
When combined, these three files—the root, intermediate, and entity—form a chain of trust.
This proves that the certificate issued on the website is valid and legitimate. But what happens when the root CA certificate expires?
When a root CA Certificate expires, how does it affect me?
When the root CA certificate expires, it would mean that operating systems will invalidate the certificate. It will affect all certificates down the hierarchy chain discussed above.
It may cause service outages, website, software, and email client downtimes, bugs, and other issues. Because computers, devices, and browsers will no longer trust certificates issued by the CA with an expired root certificate, it would also mean that older devices that have not received an update or those that run on old software releases might run into some major issues and at worst, they might stop working.
An expired root CA certificate can have significant consequences for your website and online operations. Here are some of the potential impacts:
-
Disrupted Website Functionality
When a root CA certificate expires, your website may become inaccessible to visitors. This can lead to lost business, damage your online reputation, and negatively impact your bottom line. -
Damaged Online Reputation
Visitors may be hesitant to trust a website with an expired certificate, as it can indicate security vulnerabilities or a lack of attention to detail. This can lead to a decline in website traffic, customer confidence, and overall online reputation. -
Security Vulnerabilities
An expired root certificate can compromise the security of your website, making it vulnerable to attacks such as man-in-the-middle attacks and phishing scams. These attacks can result in data breaches, financial losses, and legal liabilities.
It's essential to monitor your root certificate's expiration date and renew it well in advance to avoid these negative consequences.
What can I do to resolve issues from the expired root CA certificate?
On the surface, the fix for the problem looks simple: Root CA certificates need to be updated but not all devices receive an update. When they do, not all of them get installed.
When dealing with issues from an expired root CA (Certificate Authority) certificate, you can take the following steps to resolve the issue and ensure continuity of secure communications:
- Install a Cross Certificate
A cross certificate can be used to extend the validity of a certificate chain if the CA’s root certificate has expired. This option is useful if the expired root certificate is cross signed by another trusted root certificate.
You can install the cross certificate into the trusted root certificate store of the systems or devices affected by the expired root CA. This step ensures that the trust chain can continue without issues.
Steps to Install Cross Certificate:
- Obtain the cross-signed certificate from the Certificate Authority.
Import it into the trusted root certificate store on affected systems.
Test to confirm that the certificate chain is now recognized and functioning correctly. - Replace with a New Root CA
If a cross certificate is not available, you may need to replace the expired root CA certificate with a new, valid one.
This involves:-
Obtaining a new certificate from the Certificate Authority.
-
Distributing and installing the new certificate across all relevant systems and devices.
-
Ensuring that all intermediates and end-entity certificates are linked to the new root certificate.
-
- Update Software or Devices
Some older software or devices may not have up-to-date root CA certificates. In these cases, you can:-
Update the software to the latest version, which should include an updated list of root certificates.
-
Manually install the new root CA certificate in the software’s trust store if updating is not an option.
-
- Verify the Certificate Chain
After installing the cross certificate or replacing the root CA, verify that the certificate chain is valid using certificate checking tools (e.g., OpenSSL).
Ensure that all intermediate certificates are valid and correctly linked to the new root.
If you rely on certificates for secure communications, as most of us do these days, taking the time to examine your current validation chain is critical.
Website security is a must for all businesses. Website downtimes due to expired certificates can compromise your website’s security, company’s credibility, and client’s trust. As one of the longest-standing CAs, our certificates are trusted by APAC’s leading institutions and organizations.
A Wake-Up Call for CA Security
Recently, Google announced it would no longer trust certificates issued by a major Certificate Authority (CA), due to a series of compliance failures. This decision stemmed from Google's loss of confidence in their ability to uphold rigorous security standards. The incident caused significant disruption for organizations relying on their certificates, highlighting the importance of robust certificate management practices.
Some of the compliance failures included:
-
Failure to renew root certificates: They have allowed several of their root certificates to expire without renewing them, leading to widespread certificate revocation.
-
Insufficient audit trails: They were unable to provide adequate documentation to demonstrate compliance with security standards.
-
Weak internal controls: Their internal controls were deemed insufficient to prevent and detect security breaches.
The impact of Google's decision was far-reaching:
-
Disruption of digital services: Websites, email, and other online applications that relied on their certificates were affected.
-
Security vulnerabilities: Organizations using the said certificates were exposed to potential security risks.
-
Financial losses: Businesses may have incurred financial losses due to downtime and reputational damage.
In response to this incident, organizations and Certificate Authorities must take proactive steps to manage their digital certificates:
-
Monitor certificate expiration dates: Regularly check the expiration dates of all certificates in your organization's infrastructure.
-
Implement automated certificate management: Use tools to automatically monitor and renew certificates before they expire.
-
Have a backup plan: Develop a contingency plan to address certificate expiration issues, including procedures for renewing certificates and restoring services.
At GlobalSign, we offer a comprehensive suite of certificate management solutions to help organizations mitigate the risks associated with certificate expiration.
-
Automatic Certificate Management Environment: Our automated tools can monitor certificate expiration dates, renew certificates before they expire, and provide alerts to administrators.
-
Certificate Lifecycle Management: We can help you manage the entire lifecycle of your certificates, from issuance to revocation.
-
Advanced Monitoring and Reporting: Our monitoring tools can provide real-time visibility into your certificate infrastructure, helping you identify and address potential issues.
-
Expert Support: Our team of experts can provide guidance and support to help you manage your certificates effectively.
By partnering with us, your organization can:
-
Reduce the risk of certificate-related disruptions
-
Improve security and compliance
-
Streamline certificate management processes
-
Benefit from expert guidance and support
Renew Root CA Certificate with GlobalSign
Root certificates are a critical component of digital security, ensuring the trust and validity of other certificates in your organization. If it is nearing expiration, it's essential to renew your root CA certificate promptly to avoid disruptions and maintain a secure online presence.
GlobalSign offers a streamlined process for renewing your root certificate:
-
Contact our support team: Reach out to our experts for assistance with the renewal process.
-
Provide necessary documentation: We may require certain information to verify your identity and ownership of the certificate.
-
Pay the renewal fee: The renewal fee will vary depending on your specific certificate type and subscription plan.
-
Receive your renewed certificate: Once the renewal process is complete, you'll receive the renewed root CA certificate.
By entrusting your root certificate renewal to GlobalSign, you can benefit from our expertise, efficient processes, and commitment to customer satisfaction.
Don't let an expired root certificate jeopardize your organization's security. Contact us today to renew your root certificate and ensure the continued trust and integrity of your digital infrastructure. If you ever decide it is now time to make the switch, we can help
make the CA transition easy. We offer various SSL/TLS certificate options to save your company from inconveniences:
- Domain Validated (DV) Certificates
Reliable base-level encryption for TLS with automated and immediate issuance (within a few minutes). - Organization Validation (OV) Certificates
Strong SSL/TLS protection with instant identity information, with a vetting process that often takes only 1-2 business days. The certificate will show the corporate identity and ownership of the domain name. - Extended Validation (EV) Certificates
The highest class of SSL/TLS available today. Its presence is an indicator of the website’s validity and that it is owned and registered by a verified, legitimate business. The vetting process often takes 3-4 business days.
Our certificate management platforms can be accessed after obtaining any of our certificates to make your certificate management more seamless and flexible. Not only does this help you easily manage digital certificates and subscriptions, but also ensures your business will never experience the burden of certificate expiration and downtimes.
For a complete list of all GlobalSign products, click here.
Conclusion
A root CA is the foundation of the public key infrastructure (PKI) system. It issues certificates that verify the identity of other entities, such as websites and servers. Root CAs have a limited validity period, so it’s essential to monitor your root CA’s expiration date and renew it well in advance to avoid disruptions and maintain the security of your digital infrastructure. By following best practices for root CA certificate validity, such as setting up automatic renewal reminders and working with a reputable CA provider, you can ensure the continued trust and integrity of your digital operations.







