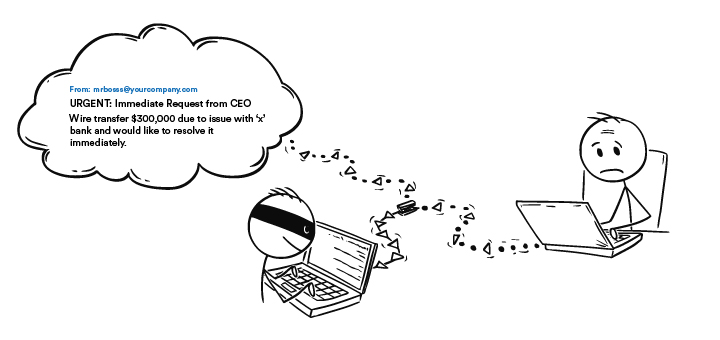
Pretend for a minute that you are a senior accountant who just attended a training about phishing. You think that you are equipped with the proper knowledge to spot threat actors. Weeks have passed and as you go about your day answering emails from clients and coworkers, you come across an email sent from your boss with the subject, "URGENT: Immediate Request from CEO".
You open the email and your boss claims that there's a "pending invoice" to one of your clients and requests for an immediate wire transfer "in the amount of $300,000" due to "issue with 'x' bank and would like to resolve it immediately". Your boss says he cannot take calls and to treat the email with utmost confidentiality. To add icing to the cake, he claims that the transfer must be issued within the day, otherwise it would cause a big blow to the company. Instructions have been given and you feel like you only have a limited time to complete this transfer.
You panic.
The title says 'urgent' in all-caps and it asks you to wire transfer to an account unfamiliar to you. You don’t want to mess this up by prolonging it and it's time to fix this issue ASAP. You look at the email address. It's from your boss, there’s no mistaking it. You check the directory because it indicates mrbosss@yourcompany.com.
You pause.
Something doesn’t sit right, you think to yourself.
You look over the email again and noticed your boss's email has an extra "s". You’re just one letter away from losing three hundred thousand dollars. Few more clicks from committing the biggest regret of your life. You immediately report this to your company and raise awareness.
According to the FBI's Internet Crime Complaint Center (IC3), Business Email Compromise scams have caused more than $26 Billion in losses in the last four (4) years despite BECs accounting for only 7% of spear-phishing attacks.
Business Email Compromise (BEC) is a specific type of phishing that makes use of social engineering to trick people into falling into their traps, which are often requests asking for money to be transferred into accounts or obtaining sensitive information of a specific target. BEC typically targets high-level executives, CEOs, or managers in the HR or finance departments.
As an employee, it is always important to be very vigilant and analyze each email received carefully. To avoid falling for a BEC scam, here are some points to look out for when receiving an email that involves an action to be taken.
Receiving a request not to follow the regular authorization procedures
Threat actors go out of their way to make sure that their victims turn a blind eye to internal protocols. Many companies have specific rules to follow, especially when it comes to money transfers. However, when a seemingly legitimate email requesting for a transfer comes from a senior staff or high-level executives, it may be easy to ignore protocols altogether. If you receive an email requesting for such, do a background check and make sure that the request is coming specifically from who the person claims to be. Unusual request contradictory to internal procedures are a huge red flag you should watch out for.
Instructions on how to proceed may be given later
Often, threat actors send initial email to hook the victim into responding. This initial email may not immediately request for a transfer of money or information, but once the victim replies, instructions will be given.
Request for a wire transfer
The most common of all BEC attacks is the request for a wire transfer. Once you see an email requesting for one, make sure to do a background check and see if the person sending the email is actually who they claim to be.
Unusual direct contact from a senior official
If it’s uncommon for a senior official, especially one claiming to be your CEO, to contact you and request for the transfer of sensitive information and sum of money, it’s time to pause and analyze if this person is really your boss.
Request for absolute confidentiality
Watch out for phrases such as ‘confidentiality’, ‘the company trusts you’, ‘I am currently unavailable’, ‘cannot accept calls’, and other variations of such phrases. These phrases often raise a red flag as threat actors do not want their victims to inform anyone else about their hacking tendencies and influence their decision making.
Pressure and a sense of urgency
Threat actors use the urgency tactic to skip the evaluation procedure of the victim and make them act fast without thinking twice or hesitating. Thus, most BEC scams make use of words that imply urgency. Most of these emails closely mimic a legitimate email request such as “urgent wire transfer” which is why it’s important to take a closer look on every single detail about the email. If anything raises suspicion, refrain from proceeding with the transaction.
Threats or unusual flattery/promises of rewards
Most threat actors use flattering language and give compliments to distract the employee from the unusual requests they are being given. It’s easy to fall for these scams once the employee is hooked and swayed by being “trusted” by the boss. When faced with a suspicious email, it’s important to check all angles and make sure that the email is not fraudulent.
Misspellings and use of spoof emails
Threat actors make use of very similar email addresses that may be overlooked by the victim especially when mobile devices are used. Among the variations include letter differences in email addresses (e.g. linkcorpo@vbox.com to ilnkcorpo@vbox.com).
GlobalSign publishes blog posts every week about different topics involving online security and identity. We also offer comprehensive certificate management such as S/MIME for email encryption and added safety to protect emails from unwanted access. To learn more about the services we offer, you may visit our official website.